
CHAPTER 15. DIGITAL TRANSFORMATION OF PUBLIC POLICY
15.5 Cybersecurity and information security
In today's conditions of rapid development of innovative technologies, people often confuse or confuse three not quite identical concepts:
1) information security (IS);
2) computer security, i.e., information technology (IT) security;
3) cybersecurity. Several definitions and comparative analyses are published online.
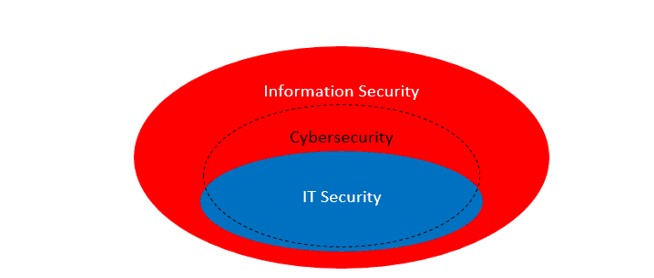
Information security.
Information security (IS), by and large, is the security of any information, including paper documents, voice information, information in people's brains, and so on. This discipline appeared several thousand years ago. That is, conditionally, with the appearance of the first encryption algorithms, if not earlier.
Traditionally, this category also includes issues of state security, propaganda, censorship, social manipulation, and so on. There are even state laws on information security that have little to do with modern IT security.
Also, information security often includes some neighboring security areas, especially for organizations that actively use IT. We are talking about physical security, personnel security, security of relations with third parties, business continuity, etc. As an authoritative example, we will cite the international standard for managing the security of organizations ISO 27001. The key two words in the name of this standard are «information security», although the standard itself contains some content outside of purely information security.
The three pillars on which information security is based are integrity, availability, and confidentiality. These requirements apply not only to electronic information, but also to «paper», oral, etc.
Thus, information security is a classic name for a discipline that covers a wide range of information security and related issues.
Information technology security.
IT security (computer security, digital security, IT security) – everything seems to be clear here. Protection against hackers, viruses, spam, phishing and many other threats that arise mainly from the Internet. This protection is most often implemented by reducing certain organizational or technical security vulnerabilities.
In more formal terms, IT security is about ensuring the integrity, availability, confidentiality, and other security requirements of computing and communications technology and the information it stores, processes, and transmits.
However, as soon as we start to understand IT security a little more deeply, there are many related tasks like protecting against social engineering, managing security performance, providing security guarantees, meeting regulatory security requirements, insuring information risks, ensuring business continuity, and dozens of similar tasks.
These tasks no longer fit into purely IT security, and require the competencies of not only IT specialists, but also economists, managers, lawyers, financiers, psychologists, teachers, and some other professions. It may seem to some that these professions are not so technologically advanced, and as if they are secondary in security. But if you look at security, it all comes down to risk management. And what to do with risks is ultimately decided by economics and mathematics.
Thus, IT security, moving to the level of competent system management, sooner or later, again comes down to information security in the understanding of the ISO 27001 standard (see paragraph 1 above).
Cybersecurity.
Cybersecurity or cybersecurity (without the hyphen) is the most ambiguous term. Many people believe that cybersecurity means the same thing as IT security. Like a modern synonym and buzzword. Some people believe that cybersecurity is a new level of IT security, linking its appearance to major threats, vulnerabilities, or incidents. Some people think that cybersecurity is the same as information security. So after all, what is cybersecurity – IT security, information security or something else? We'll figure it out.
It all started with the term «cybernetics». It was coined by Andre-Marie Ampere in 1834 and developed by Norbert Wiener in 1948. Cybernetics in the modern sense is a discipline about information in complex control systems. For example, in a computer, a person, or a society.
In the modern context, the prefix «cyber-» has been widely adopted and reinterpreted thanks to the Canadian-American science fiction writer William Gibson. In his 1984 novel «Neuromancer», he coined and popularized the term «cyberspace» to describe virtual reality and global communication networks. His work has had a profound impact on popular culture and shaped the modern understanding of the digital world.
William Gibson used the prefix «cyber-» precisely because of its positive, organizing meaning, to emphasize the contrast between the ideals of governance and the dystopian realities that can arise from the uncontrolled development of technology. His work served as a reminder of the dual nature of progress: technology has the potential to both improve lives and create new forms of risk and inequality. The choice of the prefix «cyber» was a conscious artistic device that allows you to explore the themes of control, freedom and human nature in an era of rapid technological development.
As a result, the prefix «cyber-» became associated with digital technologies, computers and the Internet.
Cybersecurity in the modern sense – is the protection of digital systems, networks and data from cyberthreats originating from cyberspace. It focuses on preventing cyberattacks, unauthorized access, data theft, and other digital threats.
It is purely technical, and when we use the word «cyber» in combination with the word «security», which means «coxswain on a ship» or «rule» in Greek, we are actually talking about «taxiing», that is, about security management.
Returning to cybernetics, which gave us the prefix «cyber», cybersecurity can mean the security of information in complex control systems. At the same time, such security itself is a complex management subsystem. So in any case, it comes down to security management.
It turns out that if you look at the origins, cybersecurity is information security management in the understanding of the same ISO 27001 standard. In other words, it is a set of processes and tools for managing the organization's security that is used to protect against cyberattacks.
Thus, we tried to unbiasedly understand the differences between information security, IT security and cybersecurity. It is not for nothing that each of these concepts is associated with security management. It is good management that gives security value[211].
Ensuring cybersecurity of foreign experience and Kazakhstan.
Since the beginning of the twenty-first century, political scientists and cybersecurity experts have warned that cyberspace will become a new battleground between States.
Many countries now pay special attention to cybersecurity in public administration. Thus, cybersecurity issues are directly related to national security.
However, cybersecurity –is much more than information security: It is not only aimed at protecting information assets, it is also protecting people and their interests. Moreover, the crucial factor that transformed this problem from a technological security problem to a political security problem was the realization that valuable assets, critical infrastructure and the destruction of which could have serious consequences for the state, are increasingly dependent on digital technologies for various functions.
High-level cyber incidents affect not only individuals and companies, but are also seen as a threat to the state, society, and the economy. As a result, States are reviewing their offensive and defensive actions and strengthening their strategic plans for the use of cyberspace.
In the era of digitalization , cyber attacks destabilize not only the internal affairs of states, but also, possibly, other states in the future. Cyberwarfare is a new way to destroy important geopolitical targets. If we take Russia and the United States as an example, there have been several incidents in cyberspace between them that can be considered components of cyberwarfare. For example, in 2016, the United States accused Russia of trying to influence the outcome of the presidential election by cyberattacking the email servers of the US Democratic Party. Other States that undermine economic, military, and political goals are also far superior to traditional sanctions.
USA. In 2010, the Stuxnet network worm developed in the United States disabled some of Iran's uranium enrichment equipment. This was a turning point for US security. The ambitious plans of the United States are quite proactive in addressing cybersecurity issues. The U.S. Government is adopting its cyber strategies at the national level.
In 2022, the US government approved a new body, the Bureau of Cyberspace and Digital Policy. They are responsible for dealing with threats to national security, addressing economic issues related to the cybersphere and US digital policy, and contributing to the protection of LOGISTICS.
In global politics, cybersecurity is gaining huge momentum and is becoming a priority for politicians. The war and the past pandemic are actively boosting the growth of the cybersecurity market. The EU and US governments are promoting additional security procedures at the state, municipal and private levels. Due to the geopolitical security situation, more organizations have started investing their resources and are even reviewing their cybersecurity strategy.
Estonia is one of the leaders in the field of digitalization and cybersecurity. Legislative frameworks and strategies, as well as government actions, contribute to creating an innovative and secure digital environment. In 2009, Estonia adopted the law on the «electronic state», which provides for the digitalization of all public services and processes. In 2011, Estonia adopted a Cybersecurity Law that requires critical infrastructure (such as banks, energy systems) to be regularly audited and secured.
Estonia is also highly regarded in the field of cybersecurity, thanks to its cyber strategy and effective response system to cyber threats. The Estonian Information System Authority has been established to coordinate network security activities. (Estonian Information System Authority The Center provides advice, vulnerability analysis, and responds to cybersecurity incidents.
Estonia actively cooperates with other countries, the European Union and NATO in the field of cybersecurity.
The European Union. European countries are also not far behind the United States, and the UK government has already set its goal to become the hegemon of cybersecurity. In order to reach the level of a «global cyberpower», the UK's National Cyber Security Center is actively increasing protection and prioritizing funding specifically in its cyberspace defense agencies.
Similar protection strategies are also observed in other countries such as China, Canada, and Israel. These countries understand how important it is to approve the implementation of cyber protection not only at the national level, but also at the public level.
Republic of Kazakhstan. Modern artificial intelligence (AI) technologies and statistical data analysis are playing an increasingly important role in the development and implementation of public policies. In Kazakhstan, digitalization of governance is becoming a priority, and AI helps make informed policy decisions based on big data. At the same time, the development of digital technologies requires increased attention to cybersecurity and information security issues.
In the cyber readiness rating compiled by the International Telecommunication Union (ITU) UN, Kazakhstan ranked 31st in the world. This rating takes into account various aspects, such as legal, technical and organizational measures, as well as development potential and cooperation with other States. It is important to note that just a few years ago Kazakhstan was ranked 83rd. This demonstrates the country's significant efforts in the field of cybersecurity.
To achieve such a breakthrough in cybersecurity, several legislative changes have taken place. In particular, a list of critical objects and information systems (CSIS) was developed, including 514 objects. This makes it possible to identify objects whose functioning is critically important for various spheres of life and state security.
To achieve such a breakthrough in the field of cybersecurity in Kazakhstan, significant changes were made to the legislation. One of the key legislative innovations is to identify critical facilities and information systems (ICOs) that play an important role in ensuring the security and vital activity of the state. These facilities include systems responsible for heat supply, electricity supply, health care, transportation, and other areas of life that are critically important to society.
The status of «critical object» imposes on them increased requirements for information security. Owners of such facilities are required to create their own operational information security center or purchase the services of an operational center from third-party organizations in accordance with the legislation of the Republic of Kazakhstan. This ensures a more effective response to potential cyber threats and improves the overall cybersecurity of the country.
In 2017, Kazakhstan adopted the state program «Digital Kazakhstan» and the concept of cybersecurity (Cybershield Kazakhstan). An important task is the active development of cybersecurity in public administration. Issues in cyber defense are directly related to national security issues of the state. The goals of the Kazakhstan Cyber Shield concept include protecting critical information and communication infrastructure (ICOs) facilities, ensuring the security of the government institutions of the Republic of Kazakhstan and the personal data of citizens themselves, as well as contributing to the development of cyberculture in society as mentioned earlier. But as with any strategic documentation, there are some problems with implementing the concept of cybersecurity. This is due to the lack of resources for the full implementation of the plans, and inefficient coordination between the ICRIAP and CIB bodies is observed.
Cybersecurity and information protection.
With the development of digital technologies, the risks of cyber attacks and data leaks are increasing. Kazakhstan is taking measures to ensure cybersecurity, including:
- the state program «Cybershield of Kazakhstan», aimed at protecting critical information infrastructure;
- development of the National Cybersecurity Coordination Center;
- strengthening the protection of personal data of citizens;
- creation and implementation of cyber threat monitoring systems;
- increasing the digital literacy of the population.
Challenges and prospects.
Despite the advantages, there are challenges:
- lack of qualified specialists in the field of AI, data analysis and cybersecurity;
- a thunderstorm from cybercriminals and the need to strengthen security measures;
-the need to integrate various state systems.
Development prospects include:
- approval of the national strategy on AI and cybersecurity;
- development of state platforms for data analysis and information security;
- strengthening international cooperation in the field of AI, digital transformation and cyber defense.
Thus, the use of AI and statistical analysis in the development of public decisions in Kazakhstan significantly increases the efficiency of management. The development of these technologies, along with strengthening cybersecurity measures, will allow Kazakhstan to become a leader in digital public administration and ensure sustainable socio-economic development.
Control questions
- Name the key stages of digital transformation of public policy.
- What technologies are the basis for digitalization of public administration?
- How does digital transformation affect the efficiency of government agencies?
- What are the risks and challenges associated with the digitalization of public policy?
- How does the introduction of artificial intelligence change political decision-making processes?
- How does digital transformation affect government transparency and accountability?
- What is the role of Big Data in the development and implementation of public policies?
- How does digitalization change the interaction of citizens with government agencies?
- How can artificial intelligence improve the efficiency of government decision-making?
- What areas of public administration already use AI, and what are the prospects for its implementation in other areas?
Questions for discussion
- Digital transformation of public administration in Kazakhstan is one of the key areas of modernization of the state apparatus. What technologies and solutions can play a crucial role in this process? What risks and barriers (infrastructure, legal, human resources) can slow down the development of the digital state? How to ensure a balance between digitalization and preserving the rights of citizens to protect their personal data?
- What mechanisms of artificial intelligence can be used to detect and prevent corruption in public bodies? What are the potential risks associated with the introduction of AI, including issues of biased algorithms, personal data protection, and effective oversight of their work?
- What key principles and approaches from the international experience of using AI could be adapted in Kazakhstan, taking into account the national characteristics of the public administration system?
Case studies
Case 1. Introduction of e-government in Estonia.
Estonia is a pioneer in the digitalization of public administration thanks to the e-Government system. Citizens can receive almost all government services online, including business registration, filing tax returns, and even participating in elections via the Internet. This system is based on the «once-only principle», which eliminates the need to repeatedly provide the same information to government agencies.
Tasks:
- What key elements of the Estonian e-Government model could be adapted to in Kazakhstan?
- What are the main barriers to implementing e-government in Kazakhstan (technical, legal, institutional)?
- How much is the population of Kazakhstan ready to switch to fully digital public services?
- what risks are associated with the digitalization of public administration (personal data, cyber threats, digital inequality)?
- How can Kazakhstan use Estonia's experience in the field of digital identification of citizens (for example, e-Residency)?
Q: Can the development of electronic voting affect the transparency of elections in Kazakhstan?
Case 2. Using artificial intelligence in social policy forecasting (Singapore).
Singapore uses artificial intelligence (AI) algorithms to analyze data on employment, income, demographic trends, and other socio-economic indicators. This allows the Government to develop more accurate social support measures, identify vulnerable groups, and predict the long-term consequences of its decisions.
Tasks:
- What types of data could be used in Kazakhstan for predictive analytics in social policy?
- What ethical and legal issues arise when using AI in predicting social policy?
- But when is Kazakhstan ready to introduce such technologies? What structures could be responsible for their development?
- How can we minimize algorithm errors and their potential discrimination against certain population groups?
- What are the advantages and risks of automating social decisions?
- Can the use of AI help solve problems of regional development and social inequality?
Case 3. «Cyber shield of Kazakhstan» state cybersecurity program.
The Cyber shield of Kazakhstan program is aimed at protecting state information systems from cyber attacks and ensuring the security of digital data. It includes monitoring of cyberthreats, development of protection mechanisms, and international cooperation in the field of cybersecurity.
Tasks:
- What are the main threats to digital security in Kazakhstan at the moment?
- What are the strengths and weaknesses of the Cyber shield of Kazakhstan program?
- What international practices in the field of cybersecurity could be useful for Kazakhstan?
- How can we improve the digital literacy of the population in cybersecurity issues?
- What measures should be taken to protect personal data of citizens in the context of digitalization?
- How can the risks of state control over digital data be minimized while maintaining a balance between security and human rights?
[211]Buldyzhov V. Cybersecurity. Information Security, IT Security – What’s the Difference? https://www.h-x.technology/ru/blog-ru/infosec-itsec-cybersecurity- Date of access 27.03.2025